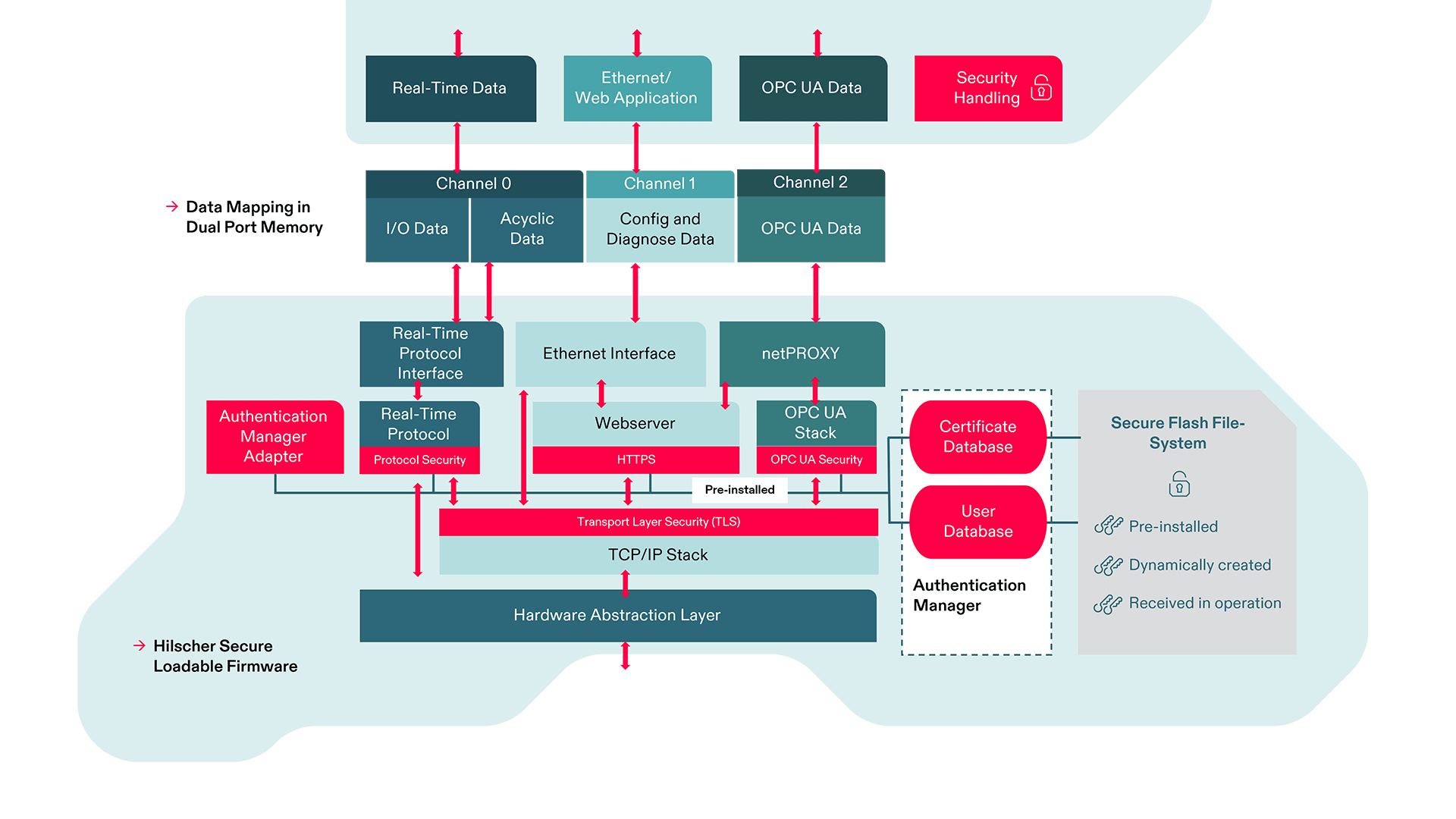
The hardware requirements for embedded security for field devices have already been taken into account into the netX 90 chip architecture. Your device needs to authenticate itself within your system, so the firmware must have the appropriate integrity for this. The transmitted data should be encrypted to prevent unauthorized access and to offer protection against data manipulation. Role definitions ensure that only authorized users are allowed to access the device or to make changes to the device configuration and software.
All netX hardware and firmware mechanisms ensure integrity, authenticity, confidentiality and authorization and thus the availability of the device and the system.
Our firmware is optimally adapted to the netX 90 hardware for these security tasks and uses the built-in hardware accelerators to make your device compatible to standards such as IEC 62443.
Multiprotocol communication in your product – our chips and modules for your highly integrated solutions.
Integrate machines and devices into your network – our turn-key communication solutions make it easy regardless of the network standard.
Centralized edge management made easy - your holistic IIoT platform for device and application management
The right communication solution for your industry – rely on Hilscher’s years of experience as the market leader in automation.
From legacy fieldbuses to Industrial Ethernet and the networking of modern sensors right up to the cloud – Hilscher’s industrial communication solutions in action.
Our IO-Link white-label products put the power of Hilscher’s communication capability in your own brand.
Our processors with variable protocol stacks make up our core technology. They are the foundation of many of our solutions. We also give you access to your machine data with our edge management solutions, paving the way to Industry 4.0.
Do you have any questions? Reach out to us or to one of our partners!
Under Downloads you’ll find numerous drivers, tools and manuals for our products.
We have been the market leader for industrial communications for over 35 years. 35 years in industrial applications and forward-looking research and development.
Find out what makes us who we are.
News, background information and a schedule of events where you can meet us – stay up to date on everything related to Hilscher and industrial communication.